HFS Research Podcast: The Next Wave with Bill...
Bill McDermott (Chairman and CEO of ServiceNow) and Ravi Kumar (CEO of Cognizant) join HFS Research Chief Analyst Phil Fersht to explore how AI is revolutionising enterprise...
Read MoreThirdera generates transformation, digitisation, and automation for our customers at the speed of NOW.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.
We help organisations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.

.jpg?width=500&height=276&name=filter%20group%20of%20people%20at%20desk%20laptop%20laughing%202021-10%20(1).jpg)


Insurance Provider Projects $75MM Gain in Business Value from Asset Management Transformation
Read more-1.jpeg?width=500&height=276&name=Indiana%20Department%20of%20Transportation%20Case%20Study%202023-03%20(3)-1.jpeg)
.jpg?width=500&height=276&name=Multichannel%20pipette%20tips%20reaction%20mixture%20plastic%20wells%202022-05%20(1).jpg)
.jpg?width=500&height=276&name=group%20-%20statistical%20analysis%202023-03%20yellow%20pink%20(1).jpg)
Balancing mission-driven goals with operational efficiency requires innovative solutions that can streamline processes and enhance programme delivery without straining budgets.

UN Agencies Rely on Thirdera and ServiceNow to Support the Ukrainian Aid Response
Read moreDigitise and automate workflows to enhance the customer experience, online and in-store.

.jpg?width=500&height=276&name=Servers%20data%20center%20room%20with%20bright%20speed%20light%202022-05%20(3).jpg)
Global SAP on Cloud Leader, Lemongrass, Embarks on Multi-Continent ITSM Overhaul
Read more

Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.
.png?width=500&height=276&name=MicrosoftTeams-image%20(638).png)

Operational Technology (OT) is a collection of hardware and software assets designed to work as an integrated system, and it's also the backbone of the business world. If a single component fails, it can have a fatal ripple effect impacting the entire environment. However, for many organisations, OT Vulnerability Management hasn't yet caught up to the modern tools available and still relies on IT protocols that are incomplete concerning the needs of OT security. This article will focus mainly on the importance of securing the Operational Technology, what are the common challenges in keeping these assets secure, and how ServiceNow and the enhanced Artificially Intelligent tools available can be used to manage and innovate security around your Operational Technology.
Let's use an everyday example to explain the ripple effect more clearly. The telecommunication we use today requires electricity to transmit information from the electric grid. The electric generators consume resources to give energy to the telecommunication, IT, transportation, and financial sectors. The transportation sector, such as railroads and trucks, delivers the resources to produce electrical energy. This same telecommunications system is used to enable communication and financial transactions in the transportation sector. Even though these industries seem unrelated, if one of them were to fail, it would cause a chain reaction that would devastate various dependent industries.
Now, apply that principle to an office building with multiple smart devices, such as thermostats, door locks, furnaces, lights, and backup power supplies. These support our offices as building management systems, fire control systems, and physical access control mechanisms, and are now often connected through a single network.
Everything that's included in the 16 Critical Infrastructure Key Resources is interlinked and interdependent to sustain society's necessities. They rely heavily on OT systems and networks to provide the resources and services for our daily needs. The security of these OT systems is essential for us to continue having everyday needs met, such as economic vitality, public health, and national security.
Operational technology is a segment of computing and communication systems consisting of hardware and software assets that monitor and manage industrial processes and equipment. It has been around longer than information technology, starting with the use of electrically powered machinery in factories and transportation systems going back to the 1790s.
OT deals with industrial operations where a sensor connected to a programmable logic controller, or other industrial mechanisms, collects output data and sends it to a service provider. This is usually a private server or cloud that stores the proprietary data for further analysis. Examples of this data could include:
Today, information is a critical and sensitive asset. Data is this age’s greatest business opportunity - and everyone seems to know it. The impact and value of data have never been more profound. Organisations that neglect to secure their data are ignoring the immense power that attackers could use against them. OT devices are supporting our systems, offices, buildings, factories, transportation, and healthcare across countless industries, and the data they collect has immense value. Safeguarding that technology is vital for two important reasons:
From the early phases of Operational Technology, their security has been largely dependent on the standalone nature of OT devices and “security through obscurity.” Once computers were introduced, OT devices have become connected to IT systems to extend the organisation's ability to monitor and adjust its Operational Technology systems. This has been good for tracking but also introduced great challenges in securing that level of technology. Approaches known from typical IT security are redesigned to align with the needs of OT devices.
Unfortunately, OT has additional priorities, such as the importance of real-time monitoring, which requires a different security protocol than is typically used for Information Technology. IT security is based on the “CIA Triad” principle, where the three concepts of confidentiality, integrity, and availability require a balanced level of focus and protection to ensure that the company is both secure and efficient in how that information is used. OT systems require the two additional concepts of real-time control and functionality change flexibility on top of the existing CIA Triad to operate effectively. This makes tracking their vulnerabilities a critical need, as well as having a well-structured remediation process. The OT devices have been connected to the internet to make them “smart” but aren’t yet smart enough to offer adequate protection when faced with an actual threat.
Operational Technology Vulnerability Management is the process of identifying, evaluating, and remediating the vulnerabilities and insecurities of OT. If these vulnerabilities are left untreated, they provide malicious actors with an avenue of attack.
A well-structured OT vulnerability management program consists of:
There are multiple stages of the vulnerability management process, some of which are just at the beginning, and some that occur continuously. We will define this under two phases: Plan and Operationalise.
The preliminary stage of the “Plan” involves some significant components such as establishing roles and responsibilities, corporate policies, and procedures for running a vulnerability remediation program. This phase is required at the beginning to establish the OT vulnerability remediation program.
The second phase termed “Operationalise,” involves regular management of these vulnerabilities. For many organisations, this phase is often flawed and faces multiple challenges across its completion.
Let's take a look at a list of the top challenges in managing OT vulnerabilities, and how you can build practices for overcoming them.
IT and OT networks have separate structures and targets. OT utilises many of its unique protocols such as Modbus, Distributed Network Protocol (DN3P), Inter-Control Center Communications Protocol (ICCP), OLE for Process Control (OPC), and International Electrotechnical Commission (IEC) Protocols. Often, the Intrusion Detection Services (IDS) rules also need to be customised for these protocols, creating a heavy need for OT vulnerabilities management for those purpose-built solutions.
Many of the OT devices are outdated, and the vendor agreements do not include frequent patches. The patch cycles are long, leading to more exposure time and dwell time for the attacker. Some OT devices usually run continuously with regularly scheduled maintenance downtime spaced five or more years apart.
Even if patch cycles are available, the time for the patches to be applied and the rest of the machine has a significant impact on the business it is running on. The downtime leads to delays in production, which is often seen as a barrier to the leadership in optimising their machine values.
The impact of downtime and uptime that vulnerability scanning could have on OT systems is a challenge to the business. The time taken to look for a vulnerability could have an interrogatory and disrupting effect on the industrial process. Active scanning for vulnerabilities is not preferred for OT devices to avoid downtimes.
The majority of the industrial companies have huge amounts of inventory data for Operational Technology, and it is stored spread across many sources, such as old spreadsheets and databases. Stale, siloed, or incomplete data prevents insights into the CI while patching. In IT, when a vulnerability is identified, you will require a Configuration Management Database (CMDB) to determine how many Configuration Items (CIs) are in scope for this vulnerability and how many can be remediated. Without the detailed profile of each OT device, this task becomes impossible in the OT space. Additionally, the asset data for OT devices would have to match the requirements of the CMDB for most tools. In those cases, a specialised CMDB for OT devices would need to be set up.
In OT environments, scanning involves some significant challenges. As discussed earlier, downtime and frequent scans can lead to inefficiencies. Some scans occur so infrequently that the related information is already outdated by the time the full scan is completed. When the vulnerabilities are verified, which could potentially count in the thousands, they often do not have any available patches from vendors or prioritisation methods to understand which critical vulnerabilities need to be addressed sooner than others. Since there is no link to a well-defined asset inventory, relating them to the most vital or at-risk assets will help determine priority. Remediating vulnerabilities, which includes patching, updating software, and bug fixes, can be a significant challenge when vendor patch releases or upgrades are often delayed.
As difficult as it is to manage the complete vulnerability management process from start to finish, it can also be challenging to maintain them. Many organisations conduct infrequent vulnerability assessments and use a separate tool for remediation which can cause errors to fall through the cracks across disparate solutions.
OT networks include various assets that are dependent on arcane protocols and specialised software that most IT administrators have little experience utilising. They are set up uniquely for every organisation and mitigating flaws in these setups demands collaboration with the product owners who are responsible for maintaining them.
The remediation of most OT vulnerabilities is mainly done manually. Even though most OT vulnerability management practices can be automated, many organisations still track their known vulnerabilities using email and spreadsheets. This leads to extensive time spent by resources to collect and manage the information that is also highly prone to errors and decreased reliability.
OT control protocols are often developed without vital security considerations and suffer from common security issues. The most common examples are a lack of authentication between endpoints and insufficiently precise controls to correctly specify recipients. Another issue is that the structure of these OT protocols is available publicly, making it easy to compromise the protocols and infect malicious software to compromise the OT devices.
In addition to all the challenges that make vulnerability management difficult for OT, security teams and OT operators must consider that public sources of vulnerability used for assessing, classifying, and prioritising are potentially using incomplete or inaccurate data. Research performed by Dragos, a platform for industrial security, has found that:
43% of vulnerability advisories contained errors making it difficult to prioritise mitigations.
64% of advisories with no patch had no vendor mitigation advice.
61% of advisories with a patch had no vendor mitigation.
73% of vulnerabilities are deemed more severe by Dragos than the Public Advisory CVSS score.
While most of the challenges make it almost impossible to develop a well-structured OT vulnerability management program, there are tools to integrate various sources and start developing a methodical process that will take resources and reliable data to provide actionable insights for remediation of OT vulnerabilities. While considering these tools, a few key factors are:
The ability to centralise your OT inventory with a well-defined CMDB.
Scanning OT Vulnerabilities across multiple classes of OT devices.
Managing the lifecycle of OT vulnerabilities in a tool with mature OT CMDB.
Grouping vulnerabilities based on vendor and defining patching timelines.
Holding your vendors accountable for fast response times and developing vendor performance tracking that measures risks and existing issues.
Utilising alternative mitigations while waiting for vendor support.
Planning fixes to avoid interruptions and downtimes.
A well-structured OT vulnerability management process is essential, but adding the integrated remediation and administrative functions of marking patches as reviewed, approved, and deployed into the same toolset would bring management to an entirely new level. With the power of ServiceNow's rich Configuration Management Database (CMDB) and the asset data Configuration Items (CIs) supporting the Vulnerability Response application, the challenges with asset inventory, protocol mapping, and downtime can be significantly reduced.
ServiceNow libraries and integrations such as the National Vulnerability Database (NVD) provide additional insights to reliable vulnerability data which is built on standards-based vulnerability management data which is maintained by the US government. This provides the authenticity for utilising the public source of vulnerability used for assessing, classifying, and prioritising vulnerabilities.
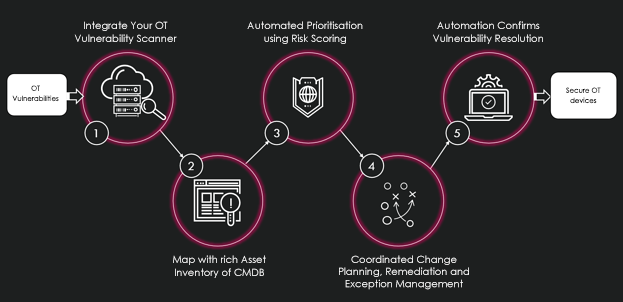
The Vulnerability Response application helps prioritise vulnerability management with the asset, risk, and threat intelligence features that can create workflows with IT for a fast and reliable response. It has a well-defined process to improve the tracking and remediation of vulnerabilities by mapping them to its associated CI, prioritising them based on the Risk Scoring mechanism, and tracking their remediation. It also documents and tracks which patches are in scope, which are available by the vendor, which devices it belongs to, and which patches have or have not been applied. This documentation is enhanced with a separate deferral workflow when it requires handling vulnerabilities that are being deferred.
The residual risk from the deferred vulnerabilities can be tracked by the Integrated Risk Management (IRM) application and can be utilised to handle the risk posed by each vendor. Vulnerabilities that are above a given risk score threshold can trigger an issue in the IRM application and send assessments to the vendor with an SLA to check if an upcoming patch cycle for this vulnerability currently exists.
Additionally, the Vendor Risk Management application can be used to tackle the challenges of analysing the vendor services timelines. The vendor is considered an entity and the control for that vendor is set as non-compliant when an issue is open for patch info. All issues are required to be closed to make the control more compliant. Reporting on vendors who have not been compliant for a specified length of time can be tracked using ServiceNow’s reporting, as well as utilising ServiceNow’s GRC indicator as a continuous monitoring system to check for Vendor Response Times.
The Performance Analytics application of ServiceNow enhances this data by utilising industry-leading metrics and benchmarks to provide real-time visibility to the Chief Information Security Officer and deliver the power of data into the hands of the respective stakeholders and subject matter experts.
We can set up appropriate scanning and remediation targets to tackle issues caused by scanning and remediation delays by integrating with the OT vulnerability scanners and enriching that data with the detailed asset inventory coming from both ServiceNow's Discovery and Nuvolo. The risk of the residual vulnerabilities can be tracked in ServiceNow’s Risk application and associated with the respective vendors using their Vendor Risk Management application. This allows you to tackle all the challenges that are currently faced by most OT Vulnerability Management teams today. When all the above applications report their data to the CISO using ServiceNow’s Performance Analytics application, the visibility into the process gives users the authority over the respective teams for influencing a highly secure environment.
Connect with our team of experts today to answer your questions about ServiceNow's Security Operations solutions and how to protect your organisation against modern security threats.
Bill McDermott (Chairman and CEO of ServiceNow) and Ravi Kumar (CEO of Cognizant) join HFS Research Chief Analyst Phil Fersht to explore how AI is revolutionising enterprise...
Read MoreAs artificial intelligence (AI) and machine learning (ML) continue to transform entire industries, organisations increasingly need robust governance and visibility into these...
Read MoreArtificial intelligence (AI) is changing how we interact with technology, driving improvements in business processes and customer experiences. Two of the most talked about...
Read MoreOriginally introduced in ServiceNow Utah, Application Portfolio Management (APM) was a part of the Strategic Portfolio Management (SPM) toolset. APM offered the capability to...
Read More